
NOTE: This post comes from Esther Barthel, MSc, solutions architect, owner of cognition IT, and a consultant to ControlUp.
Following the security bulletin released by Citrix detailing a vulnerability in Citrix Application Delivery Controller (ADC), formerly known as NetScaler ADC, and Citrix Gateway, that could lead to arbitrary code execution. In response, our Citrix ADC expert Esther Barthel created a script to help ControlUp customers detect whether or not their Citrix ADC appliance is vulnerable or if the suggested remediation has been applied.
The resulting script checks whether or not the mitigated action is configured and globally bound on NetScaler/Citrix ADC and supports the responder policy configuration. Note that this script will not perform the shell nsapimgr mitigation to avoid a potential loss of admin functionality. This script will state this as a warning as well when it is run.
The script works with a couple of arguments to trigger additional functionality/actions:
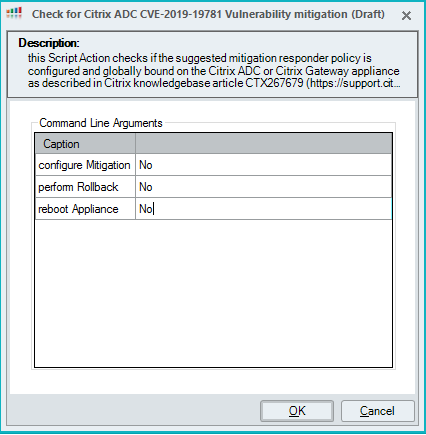
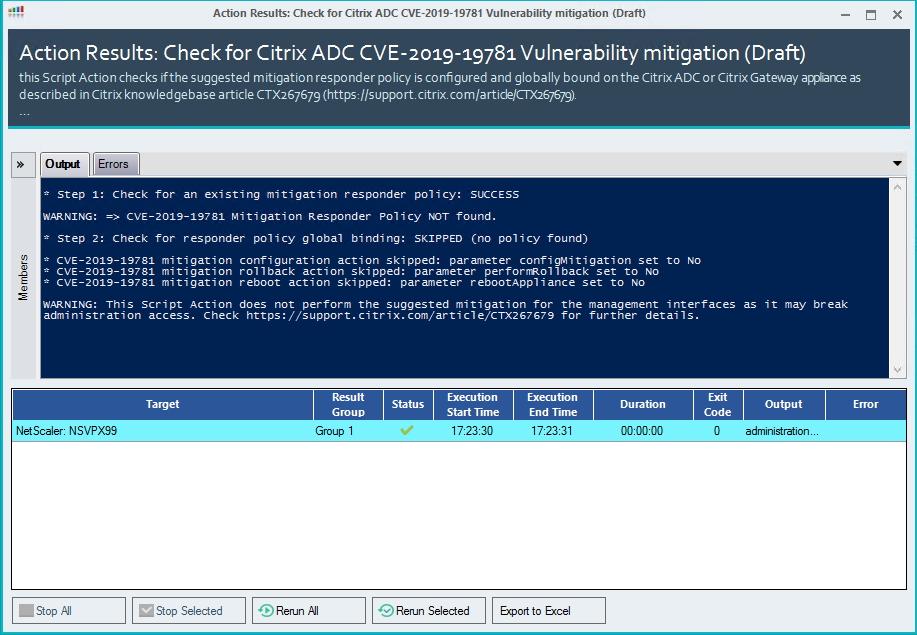
When all parameters are configured for the default value No, the script will only perform a check:
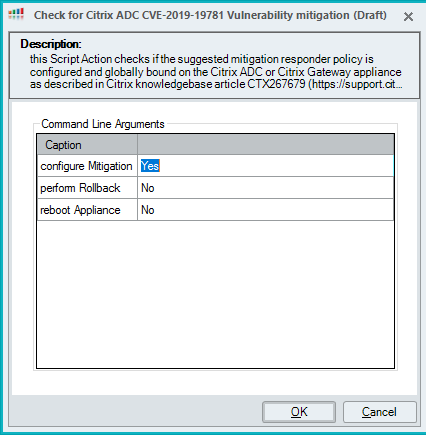
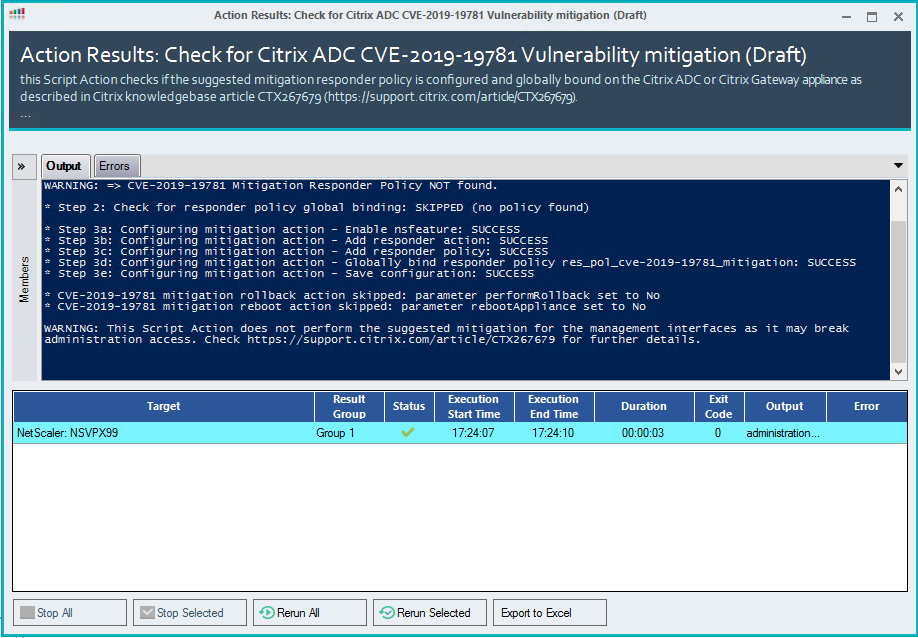
Setting configure mitigation parameter to Yes will configure the mitigation responder policy and ensure that the policy is globally bound:
If needed, you can trigger a rollback using the script by configuring the Perform Rollback argument to Yes:
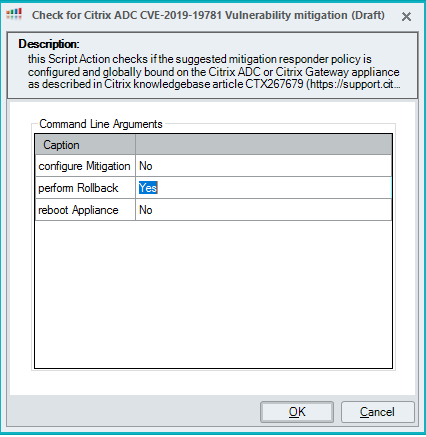
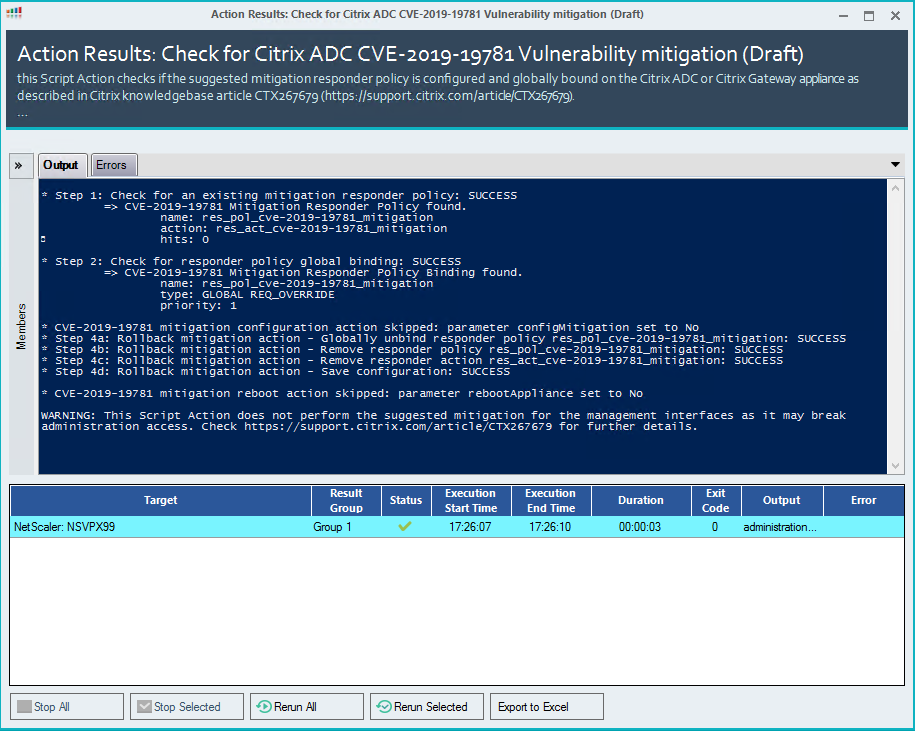
The responder policy information is based on the information retrieved with the performed check:
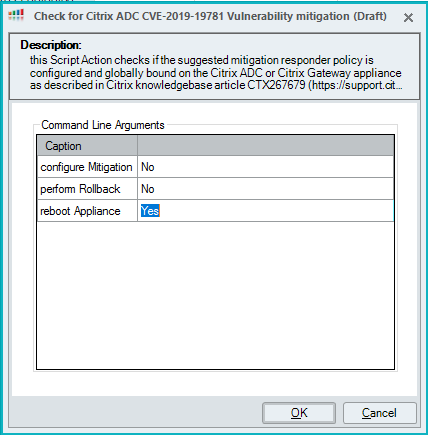
Citrix suggests a reboot to ensure any connections using the vulnerability are killed, so the script includes an argument that can be configured to Yes when needed:
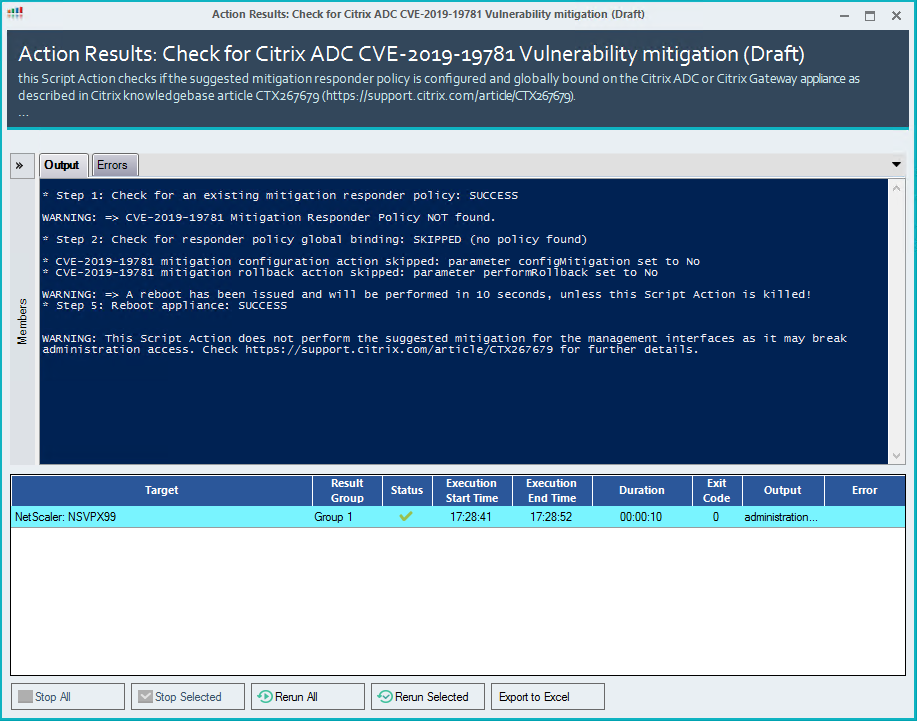
Note: Unfortunately this script is not interactive, so you can’t cancel a reboot by killing the script execution. Esther has included it in the script in case you want to run the PowerShell script as a standalone action.
To learn more about this script, go to the ControlUp Script Library and search for Check for Citrix ADC CVE-2019-19781 Vulnerability Mitigation. ControlUp customers can download the script from the ControlUp console.